Tryhackme Block Write-Up
Encryption? What Encryption?
TryHackMe Block Room
Created by : @hadrian3689
Created : 31 days old ( from the time , i am writing this writeup )
Room Type : Free
We are given a PCAP file and an LSASS dump by the challenge ( Local Security Authority Server Service (LSASS) is a process in Microsoft Windows operating systems that is responsible for enforcing security policy on the system ) . Finding encrypted SMB communication is the first thing we do after examining the PCAP file. It is clear from the room description that decryption is required. The task asks us to determine each user’s login, password, hash, flag, and potentially even the substance of the files they sent. All of this ought to be achievable with the LSASS dump and the PCAP file.
What I Found In The First Look
I downloaded the zip file , attached in this challenge and then open it in the wireshark , by just looking at the i see SMB2 authentication request by the domain\user : WORKGROUP\mrealman ,
- Then i found the file related to that in the
clients156.csvformat in the request .
- Then scrolling down i found another WORKGROUP\USER : WORKGROUP\eshellstrop
- and then i found file
clients978.csvrelated to that user he trying to access
Investigating the First User
Investigating gives feel like doing forensics ;-) . To show just packets containing NTLM (NT LAN Manager) Security Support Provider (SSP) protocol data, use Wireshark’s ntlmssp filter. A security mechanism called NTLMSSP is employed in a number of Microsoft network authentication methods, especially in setups where Kerberos cannot be used.
We got the answer of the first question of the this room , next we have to find the password for the user 1 , which is mrealman .
I found a tool on google named as PCredz . This tool extracts Credit card numbers, NTLM(DCE-RPC, HTTP, SQL, LDAP, etc), Kerberos (AS-REQ Pre-Auth etype 23), HTTP Basic, SNMP, POP, SMTP, FTP, IMAP, etc from a pcap file or from a live interface.
-f : flag is used to specify the file and -d : flag is used to specify directory
This too need the PCAP file and be able to retrieve the NTLMv2 hashes of mrealman and eshellstrop , which i was not hoping for , at least for this while .
These are the Components that are necessary to create a NTLMv2 structure ;
- Username : The username used for the NTLMv2 Authentication .
- Domain : The domain used for the NTLMv2 Authentication .
- Server Challenge : An 8-byte challenge sent by the server to the client
- NT Proof String ( NTLMv2 Response ) : The first 16 bytes of the NTLMv2 response, which is the HMAC-MD5 hash.
- Challenge blob : The remaining part of the NTLMv2 response, including the timestamp, client challenge, target information, etc.
Next, combine the required components into an NTLMv2 structure:
1
<username>::<domain>:<server_challenge>:<nt_proof_string>:<blob>
- i use the
hashcattool to crack the password of these , hashes and i only got themrealmanuser hash not the other one , and here i am hoping to get both ;-(
1
2
┌──(archtrmntor㉿kali)-[~/Desktop/thm/PCredz]
└─$ hashcat -m 5600 -a 0 "mrealman::WORKGROUP:2a9c5234abca01e7:16E816DEAD<REDECTED>" /usr/share/wordlists/rockyou.txt
flag for the mrealman user is next question , while researching i got this blog during researching Decrypting SMB3 Traffic with just a PCAP? Absolutely ( maybe.) , it tell us how to decrypt the encrypted SMB traffic to get the transferred item and extract the information and see them .
All we need key exchange key , to decrypt , which can be derived from the content of the PCAP file we have . In summary , the Random Session Key can be calculated by :
1
-Unicode (utf-16le) of password-MD4 hash of the above _(This is also the NTLM Hash of the password)_-Unicode(utf-16le) and Uppercase of Username and Domain/Workgroup together -Calculating the ResponseKeyNT via HMAC_MD5(NTLM Hash, Unicode of User/Domain above)-NTProofStr _(can be calculated but not needed as it is present in the PCAP)_-Calculating the KeyExchangeKey via HMAC_MD5(ResponseKeyNT,NTProofStr)-Decrypt the Encrypted Session Key via RC4 and the Key Exchange Key to finally get the Random Session Key
NTProofStringcan be found in thentlmssppacket
- ………so as encrypted session key.
- we can use the python script given by
Maveris lab, it not only take the passwords but also the hashes can be used directly , might be use in the case of second user bcoz we are not able to crack the hash for that user . - Here is the Python
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
import hashlib
import hmac
import argparse
import binascii
# stolen from impacket. Thank you all for your wonderful contributions to the community
try:
from Cryptodome.Cipher import ARC4
from Cryptodome.Cipher import DES
from Cryptodome.Hash import MD4
except Exception as e:
print("Warning: You don't have any crypto installed. You need pycryptodomex")
print("See https://pypi.org/project/pycryptodomex/")
raise e
def generate_encrypted_session_key(key_exchange_key, exported_session_key):
cipher = ARC4.new(key_exchange_key)
cipher_encrypt = cipher.encrypt
session_key = cipher_encrypt(exported_session_key)
return session_key
parser = argparse.ArgumentParser(description="Calculate the Random Session Key based on data from a PCAP (maybe).")
parser.add_argument("-u", "--user", required=True, help="User name")
parser.add_argument("-d", "--domain", required=True, help="Domain name")
parser.add_argument("-p", "--password", help="Password of User")
parser.add_argument("-ph", "--passwordhash", help="NTLM Hash of the Password (in Hex)")
parser.add_argument("-n", "--ntproofstr", required=True, help="NTProofStr. This can be found in PCAP (provide Hex Stream)")
parser.add_argument("-k", "--key", required=True, help="Encrypted Session Key. This can be found in PCAP (provide Hex Stream)")
parser.add_argument("-v", "--verbose", action="store_true", help="Increase output verbosity")
args = parser.parse_args()
# Validate that either password or password hash is provided
if not args.password and not args.passwordhash:
parser.error("You must provide either --password or --passwordhash")
# Upper Case User and Domain
user = str(args.user).upper().encode('utf-16le')
domain = str(args.domain).upper().encode('utf-16le')
# If password is provided, calculate the NTLM hash
if args.password:
passw = args.password.encode('utf-16le')
hash1 = hashlib.new('md4', passw)
password_hash = hash1.digest()
else:
# Use provided password hash (in hex) instead of calculating it
password_hash = binascii.unhexlify(args.passwordhash)
# Calculate the ResponseNTKey
h = hmac.new(password_hash, digestmod=hashlib.md5)
h.update(user + domain)
resp_nt_key = h.digest()
# Use NTProofSTR and ResponseNTKey to calculate Key Exchange Key
nt_proof_str = binascii.unhexlify(args.ntproofstr)
h = hmac.new(resp_nt_key, digestmod=hashlib.md5)
h.update(nt_proof_str)
key_exch_key = h.digest()
# Calculate the Random Session Key by decrypting Encrypted Session Key with Key Exchange Key via RC4
r_sess_key = generate_encrypted_session_key(key_exch_key, binascii.unhexlify(args.key))
if args.verbose:
print("USER WORK: " + user.decode('utf-16le') + domain.decode('utf-16le'))
if args.password:
print("PASS HASH: " + binascii.hexlify(password_hash).decode())
print("RESP NT: " + binascii.hexlify(resp_nt_key).decode())
print("NT PROOF: " + binascii.hexlify(nt_proof_str).decode())
print("KeyExKey: " + binascii.hexlify(key_exch_key).decode())
print("Random SK: " + binascii.hexlify(r_sess_key).decode())
- we need the python3 package to run this file , and we can use the various flag to able to retrieve the session key.
1
python3 decrypt.py -u mrealman -d WORKGROUP -p <Password> -n 16e816dead16d4ca7d5d6dee4a015c14 -k fde53b54cb676b9bbf0fb1fbef384698
- as mention in the above blog we need the session id to decrypt the SMB traffic .
- All that’s left to do is add the session ID and the computed session key to the
Edit->Preferences->Protocols->SMB2protocol settings. However, as the example below illustrates, the option expects a different representation than the one in the packet. - i am writing the writeup later , so i attached the session for the another user too in below screenshot .
- we have to format the
Session IDas4100000000100000. we need to reverse the bytes because of the endianness ( endianness is the order in which bytes within a word of digital data are transmitted over a data communication medium or addressed in computer memory, counting only byte significance compared to earliness. )
- and that’s how we successfully decrypt the SMB traffic .
- Export the SMB objects to a file .
file -> Export Objects -> SMB
sdsdf
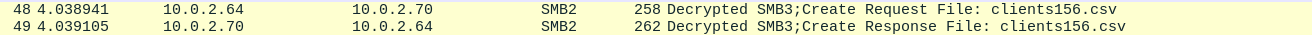
- save and open the file
clients156.csvand you got the flag for the first user .
Investigating The Second User
as we already now the second username
eshellstrop, which answer another question of the room , for next question we have to find the hash of the second user . ![[Pasted image 20240909135444.png]]We can utilize another tool name pypykatz , which can extract the NTLM hash from the LSASS dump .
1
$ pypykatz lsa minidump lsass.DMP --json | grep NThash -A10
- we can copy the hash of the
eshellstrop, which we will use with the Pcredz tool , to decrypt the SMB traffic .
- as previous the get the
NTProofstr:for usereshellstrop
- and …..same grep the
Session Key:
- and……same grep the
Session ID
- now we can use the
maverislabspython script with the different flag-u: for user-d: for domain-ph: for password hash-n: for NTProofStr-k: for session key
1
python3 decrypt.py -u eshellstrop -d WORKGROUP -ph 3f29138a04aadc19214e9c04028bf381 -n 0ca6227a4f00b9654a48908c4801a0ac -k c24f5102a22d286336aac2dfa4dc2e04
- …And repeat the steps as already known of first user.
Edit->Preferences->Protocols->SMB2
file -> Export Objects -> SMB
- Open the saved file
clients978.csv, and you got the final user flag .




![[Pasted image 20240909135739.png]](/assets/img/block/Pasted%20image%2020240909135739.png)
![[Pasted image 20240909135944.png]](/assets/img/block/Pasted%20image%2020240909135944.png)
![[Pasted image 20240909140053.png]](/assets/img/block/Pasted%20image%2020240909140053.png)
![[Pasted image 20240909140148.png]](/assets/img/block/Pasted%20image%2020240909140148.png)
![[Pasted image 20240909140308.png]](/assets/img/block/Pasted%20image%2020240909140308.png)
![[Pasted image 20240909140357.png]](/assets/img/block/Pasted%20image%2020240909140357.png)
![[Pasted image 20240909140512.png]](/assets/img/block/Pasted%20image%2020240909140512.png)
![[Pasted image 20240909140615.png]](/assets/img/block/Pasted%20image%2020240909140615.png)
![[Pasted image 20240909140711.png]](/assets/img/block/Pasted%20image%2020240909140711.png)
![[Pasted image 20240909140810.png]](/assets/img/block/Pasted%20image%2020240909140810.png)
![[Pasted image 20240909140834.png]](/assets/img/block/Pasted%20image%2020240909140834.png)
![[Pasted image 20240909141047.png]](/assets/img/block/Pasted%20image%2020240909141047.png)
![[Pasted image 20240909140935.png]](/assets/img/block/Pasted%20image%2020240909140935.png)
![[Pasted image 20240909141215.png]](/assets/img/block/Pasted%20image%2020240909141215.png)
![[Pasted image 20240909153217.png]](/assets/img/block/Pasted%20image%2020240909153217.png)
![[Pasted image 20240909141400.png]](/assets/img/block/Pasted%20image%2020240909141400.png)